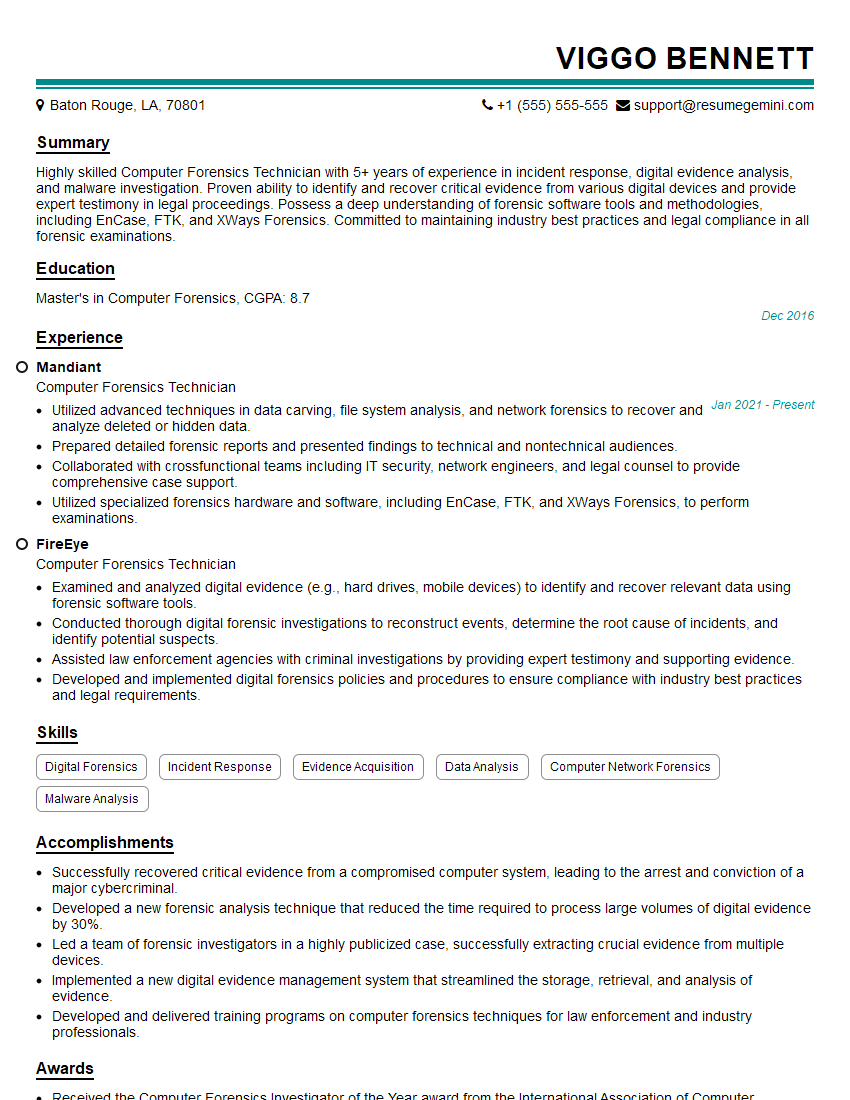
Are you gearing up for a career shift or aiming to ace your next interview? Look no further! We’ve curated a comprehensive guide to help you crack the interview for the coveted Computer Forensics Technician position. From understanding the key responsibilities to mastering the most commonly asked questions, this blog has you covered. So, buckle up and let’s embark on this journey together.
Acing the interview is crucial, but landing one requires a compelling resume that gets you noticed. Crafting a professional document that highlights your skills and experience is the first step toward interview success. ResumeGemini can help you build a standout resume that gets you called in for that dream job.
Essential Interview Questions For Computer Forensics Technician
1. How do you carry out a computer forensic investigation?
In a computer forensic investigation, I typically follow these steps:
- Identification: Determine the scope of the investigation and gather evidence.
- Preservation: Secure and preserve the evidence to prevent alteration or loss.
- Collection: Acquire and document the evidence using appropriate tools and techniques.
- Examination: Analyze and interpret the evidence to identify relevant information.
- Analysis: Evaluate the findings and draw conclusions based on the evidence.
- Reporting: Document the investigation process and findings in a clear and concise report.
2. Describe the different methods of data recovery.
File System Recovery
- Recover deleted files and reconstruct file systems using tools like Recuva and PhotoRec.
Disk Imaging
- Create a bit-by-bit copy of the storage device to preserve data in case of further damage.
- Tools used include dd (Unix) and EnCase (commercial).
RAID Recovery
- Recover data from Redundant Array of Independent Disks (RAID) configurations.
- Requires specialized tools and knowledge to reconstruct the data.
3. What are the ethical considerations in computer forensics?
Ethical considerations are crucial in computer forensics to ensure the integrity and accuracy of the investigation:
- Privacy: Respect the privacy rights of individuals involved and only access data that is relevant to the investigation.
- Objectivity: Maintain impartiality and avoid bias in the investigation and analysis.
- Transparency: Document all actions taken during the investigation and provide a clear and transparent report.
- Chain of Custody: Maintain the integrity and security of evidence throughout the investigation.
4. How do you use specialized software tools in computer forensics?
Specialized software tools are essential in computer forensics to facilitate various tasks:
- Data Acquisition: Tools like EnCase and FTK Imager to acquire data from storage devices.
- File Recovery: Tools like Recuva and PhotoRec to recover deleted or corrupted files.
- Analysis: Tools like X-Ways Forensics and Autopsy to analyze disk images, identify artifacts, and extract evidence.
- Reporting: Tools like Forensics Report Writer and NetWitness Investigator to generate clear and comprehensive reports.
5. Describe your experience in using forensic imaging techniques.
Forensic imaging involves creating an exact copy of a storage device to preserve its data:
- Disk Cloning: Using tools like dd or FTK Imager to create a bit-by-bit copy of the disk.
- Disk Mirroring: Copying the contents of a disk to another while maintaining the original sector-by-sector layout.
- Partition Imaging: Acquiring an image of specific partitions or logical volumes.
6. How do you handle volatile data in computer forensics?
Volatile data, such as memory and network traffic, is crucial in computer forensics:
- Memory Acquisition: Using tools like Volatility or FTK Imager to acquire a snapshot of the computer’s memory.
- Network Traffic Capture: Monitoring and capturing network traffic using tools like Wireshark or tcpdump.
- Live Analysis: Conducting forensics on a live system to examine volatile data before it disappears.
7. What are the challenges of working with encrypted data in computer forensics?
Encrypted data poses challenges in computer forensics due to its protection:
- Encryption Algorithms: Different encryption algorithms offer varying levels of security, making some more challenging to break.
- Key Management: Keys used for encryption may be complex or unavailable, making decryption difficult.
8. How do you stay up-to-date with the latest trends and techniques in computer forensics?
Staying up-to-date is essential in computer forensics due to evolving technologies:
- Industry Conferences and Events: Attending conferences like Digital Forensics and Incident Response (DFIR) Summits.
- Online Training and Certification: Pursuing certifications from organizations like the International Society of Forensic Computer Examiners (ISFCE).
- Research and Reading: Regularly reviewing academic journals, industry publications, and technical blogs.
9. Describe your approach to reporting your findings in computer forensics.
Reporting findings in computer forensics requires clear and concise communication:
- Executive Summary: A brief overview of the investigation and its key findings.
- Methodology: A detailed description of the techniques and tools used during the investigation.
- Results: A presentation of the evidence and analysis that supports the conclusions.
- Conclusions: A summary of the findings and their significance.
- Recommendations: Any suggestions or advice for further actions based on the findings.
10. How do you prioritize tasks and manage your workload in a fast-paced computer forensics environment?
Prioritization and workload management are crucial in computer forensics due to time constraints:
- Triage: Assessing the urgency and importance of cases to determine the order of investigation.
- Communication: Collaborating with colleagues and stakeholders to manage expectations and timelines.
- Automation: Using tools to automate repetitive tasks and streamline the investigation process.
Interviewers often ask about specific skills and experiences. With ResumeGemini‘s customizable templates, you can tailor your resume to showcase the skills most relevant to the position, making a powerful first impression. Also check out Resume Template specially tailored for Computer Forensics Technician.
Career Expert Tips:
- Ace those interviews! Prepare effectively by reviewing the Top 50 Most Common Interview Questions on ResumeGemini.
- Navigate your job search with confidence! Explore a wide range of Career Tips on ResumeGemini. Learn about common challenges and recommendations to overcome them.
- Craft the perfect resume! Master the Art of Resume Writing with ResumeGemini’s guide. Showcase your unique qualifications and achievements effectively.
- Great Savings With New Year Deals and Discounts! In 2025, boost your job search and build your dream resume with ResumeGemini’s ATS optimized templates.
Researching the company and tailoring your answers is essential. Once you have a clear understanding of the Computer Forensics Technician‘s requirements, you can use ResumeGemini to adjust your resume to perfectly match the job description.
1. Evidence Collection
Collecting digital evidence from various devices, including computers, laptops, and mobile phones.
- Preserving electronic data and maintaining its integrity.
- Documenting evidence and creating detailed reports.
2. Data Analysis
Examining digital evidence to identify and recover hidden or deleted files, emails, and other data.
- Analyzing file systems, metadata, and network activity.
- Using forensic software and techniques to extract and interpret digital evidence.
3. Expert Testimony
Testifying in court as an expert witness on the findings of the investigation.
- Explaining technical concepts to non-technical audiences.
- Providing analysis and insights based on digital evidence.
4. Case Management
Managing computer forensics cases, including coordinating with law enforcement and legal counsel.
- Prioritizing cases based on severity and urgency.
- Keeping accurate records of all investigative activities.
1. Research and Preparation
Thoroughly research the organization and the specific job requirements.
- Practice answering common interview questions related to computer forensics.
- Prepare examples of previous investigations and how you successfully analyzed and presented evidence.
2. Technical Expertise
Demonstrate strong technical skills and knowledge of computer forensics tools and techniques.
- Highlight your experience in using forensic software and hardware.
- Discuss your understanding of different file systems and data recovery methods.
3. Communication and Presentation
Possess excellent communication and presentation skills, as you may be required to testify in court.
- Practice explaining technical concepts in a clear and concise manner.
- Prepare examples of how you effectively communicated findings to legal counsel and law enforcement.
4. Ethical Considerations
Emphasize your understanding of ethical responsibilities and the importance of maintaining confidentiality and integrity in computer forensics.
- Discuss your commitment to following established protocols and legal guidelines.
- Provide examples of situations where you handled sensitive information with discretion.
5. Continuing Education and Certification
Demonstrate your commitment to professional development and staying up-to-date with industry best practices.
- Mention any relevant certifications or training programs you have completed.
- Explain your plans for ongoing education and staying abreast of technological advancements.
Next Step:
Armed with this knowledge, you’re now well-equipped to tackle the Computer Forensics Technician interview with confidence. Remember, preparation is key. So, start crafting your resume, highlighting your relevant skills and experiences. Don’t be afraid to tailor your application to each specific job posting. With the right approach and a bit of practice, you’ll be well on your way to landing your dream job. Build your resume now from scratch or optimize your existing resume with ResumeGemini. Wish you luck in your career journey!